This is our small website to try to help all the public in general and companies in particular. As Leonardo Da Vinci said: Simplicity is the highest sophistication.
Cybersecurity has become an essential part of our daily lives.
We hope you enjoy our content. Remember that you can translate the website with the language selector at the top right.
- Inside a modern Security Operations Center (SOC)A modern Security Operations Center (SOC) cannot operate in isolation. Its effectiveness relies not only on the technology and analysts… Read more: Inside a modern Security Operations Center (SOC)
- The Power of Nmap: Scanning, Enumeration, and Security Auditing ExplainedNmap is a powerful yet often underestimated network scanning tool. Many know it for basic usage like detecting open ports,… Read more: The Power of Nmap: Scanning, Enumeration, and Security Auditing Explained
- Operationalizing CVE Management: Practical RecommendationsKeeping track of CVEs (Common Vulnerabilities and Exposures) relevant to an organization’s infrastructure is neither a passive nor a one-off… Read more: Operationalizing CVE Management: Practical Recommendations
- CitrixBleed 2: Anatomy of a Critical Breach and a Crucial Test for Enterprise ResilienceOn July 10, 2025, the United States Cybersecurity and Infrastructure Security Agency (CISA) designated a critical vulnerability in Citrix NetScaler… Read more: CitrixBleed 2: Anatomy of a Critical Breach and a Crucial Test for Enterprise Resilience
- Understanding the Purple TeamThe concept of a Purple Team in cybersecurity does not refer to a specific unit with fixed functions, but rather… Read more: Understanding the Purple Team
- How to Start a Career in Cybersecurity (Part 2): Our proposed roadmapGeneral Cybersecurity Learning Path (Common to All Roles) Phase 1 – Absolute Fundamentals (for non-technical beginners): Phase 2 – Technical… Read more: How to Start a Career in Cybersecurity (Part 2): Our proposed roadmap
- How to Start a Career in Cybersecurity (Part 1): Roadmap, Specializations, and Skills That MatterEntering the cybersecurity field does not follow a single, linear path. The current ecosystem is vast and constantly evolving, requiring… Read more: How to Start a Career in Cybersecurity (Part 1): Roadmap, Specializations, and Skills That Matter
- The 7.3 Tbps DDoS Attack: A Direct Warning to Corporate Cybersecurity Defense TeamsOn May 15, 2025, a new record was set in the history of cyberattacks: a distributed denial-of-service (DDoS) attack peaked… Read more: The 7.3 Tbps DDoS Attack: A Direct Warning to Corporate Cybersecurity Defense Teams
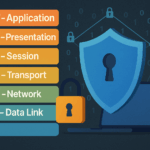
- Security in the OSI Layers: Understanding the Network to Defend ItThe OSI model is the conceptual backbone that breaks down the complexity of network communication into seven distinct layers. While… Read more: Security in the OSI Layers: Understanding the Network to Defend It
- ITDR: Identity Threat Detection and Response in Hybrid and Multi-Cloud EnvironmentsThe perimeter is dead, or rather, it has mutated. In today’s corporate environments, dominated by hybrid architectures, remote users, cloud… Read more: ITDR: Identity Threat Detection and Response in Hybrid and Multi-Cloud Environments
- Intentional Manipulation Attacks Aimed at Corrupting AI Model DecisionsThe widespread integration of artificial intelligence models into corporate systems has introduced a new risk vector: the possibility of manipulating… Read more: Intentional Manipulation Attacks Aimed at Corrupting AI Model Decisions
- What to Do if a CVE Threatens Your CompanyWhen a new CVE (Common Vulnerabilities and Exposures) emerges affecting software, operating systems, or devices within your infrastructure, it’s not… Read more: What to Do if a CVE Threatens Your Company
- The Cybersecurity Risks of Generative AI ToolsSystems based on foundation models like ChatGPT, GitHub Copilot, Gemini or Claude introduce a new set of cybersecurity risks that… Read more: The Cybersecurity Risks of Generative AI Tools
- Recent Linux Vulnerabilities: Spotlight on sudoLinux security is once again under scrutiny following the disclosure of several critical vulnerabilities in widely deployed components. One of… Read more: Recent Linux Vulnerabilities: Spotlight on sudo
- Grok 4: Technical Excellence Amid Ethical and Security ControversiesOn July 9, 2025, xAI released Grok 4 alongside its extended version, Grok 4 Heavy, with claims of advanced reasoning… Read more: Grok 4: Technical Excellence Amid Ethical and Security Controversies
- What Should I Do If I Compromise My Credentials?Realizing that your credentials have been compromised is not a remote possibility—it’s a plausible scenario in any organization or connected… Read more: What Should I Do If I Compromise My Credentials?